| Title: | Computer Forensics Analysis |
| Date: | 5th October 2000 |
| Time: | 14:00 - 16:00 |
| Venue: | Seminar Room 833, HSH Engineering Building |
Abstract:
This seminar introduces some basic techniques in Computer Forensics. It shows you how to collect evidence without interfering the activities of the inspected system. It also discusses how hackers hide their traces when breaking into a system and the methods to work against it.
Seminar Outline
cp -rp directory target_directory
Received side
nc -p 6666 -l > output
Send side
cat data |nc -w 3 receved_host 6666
Received side
/usr/local/bin/ttcp -r -B | tar xvpf -
Send side
tar cf - directory | /usr/local/bin/ttcp -t receved_host
dd if=/dev/rdsk/c0t0d0s7 of=/dev/rmt/0
dd if=/dev/rdsk/c0t0d0s7 of=/dev/rdsk/same_size_disk
dd if= /dev/kmem of=output
dd if= /dev/mem of=output
/usr/ucb/ps auxeww
to view the running process enviroment
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 467 0.0 0.2 1172 168 ? S Jun06 0:04 syslogd -m 0 INIT_VERSION=sysvinit-2.
78 previous=N TERM=linux HOSTTYPE=i386 PATH=/sbin:/usr/sbin:/bin:/usr/bin:/usr/X11R6/bin CONSOLE=/de
v/console HOME=/ PREVLEVEL=N RUNLEVEL=3 SHELL=/bin/bash runlevel=3 AUTOBOOT=YES BOOT_IMAGE=linux1 OS
TYPE=Linux SHLVL=2 _=/bin/nice
shlam 12485 99.9 22.7 15492 14112 ? RN 07:42 126:28 ./setiathome TERM=vt100
DISPLAY=ntec5:10.0 HOME=/home/shlam SHELL=/bin/tcsh USER=shlam LOGNAME=shlam
PATH=/usr/kerberos/bin:/bin:/usr/bin:/usr/local/bin:/usr/bin/X11:/usr/X11R6/bin
HOSTTYPE=i386-linux VENDOR=intel OSTYPE=linux MACHTYPE=i386 SHLVL=1 PWD=/home/shlam/set
GROUP=peter HOST=ntec5
REMOTEHOST=ntec4.ie.cuhk.edu.hk HOSTNAME=ntec5 INPUTRC=/etc/inputrc LS_COLORS=no=00:fi=00:
di=01;34:ln=01;36:pi=40;33:so=01;35:bd=40;33;01:cd=40;33;01:or=01;05;37;41:mi=01;05;37;41:
ex=01;32:*.cmd=01;32:*.exe=01;32:*.com=01;32:*.btm=01;32:*.bat=01;32:*.sh=01;32:*.csh=01;32:
*.tar=01;31:*.tgz=01;31:*.arj=01;31:*.taz=01;31:*.lzh=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:
*.gz=01;31:*.bz2=01;31:*.bz=01;31:*.tz=01;31:*.rpm=01;31:*.cpio=01;31:*.jpg=01;35:*.gif=01;
35:*.bmp=01;35:*.xbm=01;35:*.xpm=01;35:*.png=01;35:*.tif=01;35: KDEDIR=/usr LANG=en_US LESSOPEN
=|/usr/bin/lesspipe.sh %s QTDIR=/usr/lib/qt-2.1.0 HTTP_PROXY=proxy.ie.cuhk.edu.hk:8080
ps -ealf F S UID PID PPID C PRI NI ADDR SZ WCHAN STIME TTY TIME CMD 8 S nobody 1631 2506 0 41 20 60b94200 316 6087094c Jun 05 ? 0:01 /usr/httpd/bin/httpd 8 S nobody 1632 2506 0 41 20 60b4af78 316 608704ec Jun 05 ? 0:01 /usr/httpd/bin/httpd
csh> lsof -p 467
COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME
syslogd 467 root cwd DIR 3,3 4096 2 /
syslogd 467 root rtd DIR 3,3 4096 2 /
syslogd 467 root txt REG 3,3 26352 96657 /sbin/syslogd
syslogd 467 root mem REG 3,3 340663 208505 /lib/ld-2.1.3.so
syslogd 467 root mem REG 3,3 4101324 208512 /lib/libc-2.1.3.so
syslogd 467 root mem REG 3,3 246652 208543 /lib/libnss_files-2.1.3.so
syslogd 467 root 0u unix 0xc37c2ec0 502 /dev/log
syslogd 467 root 1w REG 3,3 210439 229189 /var/log/messages
syslogd 467 root 2w REG 3,3 114 229190 /var/log/secure
syslogd 467 root 3w REG 3,3 1144 229191 /var/log/maillog
syslogd 467 root 4w REG 3,3 0 229192 /var/log/spooler
syslogd 467 root 5w REG 3,3 27428 229193 /var/log/boot.log
syslogd 467 root 6w REG 3,3 0 226719 /var/log/news/news.crit
syslogd 467 root 7w REG 3,3 0 226720 /var/log/news/news.err
syslogd 467 root 8w REG 3,3 0 226718 /var/log/news/news.notice
FD is the File Descriptor number of the file or:
cwd current working directory;
Lnn library references;
ltx shared library text (code and data);
Mxx hex memory-mapped type number xx.
m86 DOS Merge mapped file;
mem memory-mapped file;
pd parent directory;
rtd root directory;
txt program text (code and data);
v86 VP/ix mapped file;
FD is followed by one of these characters, describing the mode under
which the file is open:
r for read access;
w for write access;
u for read and write access;
space if unknown and no lock character;
`-' if unknown and lock character.
csh> ltrace -p 12485 getrusage(0, 0xbffff820, 0x4013dd60, 0x4013dd60, 0x64646465) = 0 free(0x40d46008) =sprintf("outfile.sah", "%s%s", "", "outfile.sah") = 11 fopen("outfile.sah", "r") = 0x080731a8 fseek(0x080731a8, 0, 2, 0x0805de68, 0x40d46040) = 0 ftell(0x080731a8, 0x0805d001, 0xbffff868, 0x0805033e, 0x080731a8) = 5208 fclose(0x080731a8) = 0 malloc(524355) = 0x40d46008
csh> strace -p 12485
old_mmap(NULL, 1052672, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x40d46000
getrusage(RUSAGE_SELF, {ru_utime={7512, 860000}, ru_stime={12, 290000}, ...}) = 0
munmap(0x40d46000, 1052672) = 0
open("outfile.sah", O_RDONLY) = 4
fstat(4, {st_mode=S_IFREG|0644, st_size=5208, ...}) = 0
old_mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x40015000
fstat(4, {st_mode=S_IFREG|0644, st_size=5208, ...}) = 0
_llseek(4, 4096, [4096], SEEK_SET) = 0
read(4, "4 chirprate=7.926451e+00 maxpow="..., 1112) = 1112
close(4) = 0
munmap(0x40015000, 4096) = 0
kill -STOP pid ps ax|grep T to check its status
gcore -o core.file pid (for solaris)
pcat pid > dump.file (by using CTC)
kill -CONT pid
csh> strings /tmp/syslogd.dump
/lib/ld-linux.so.2
__gmon_start__
libc.so.6
longjmp
strcpy
writev
printf
stdout
getdtablesize
recv
strerror
fdopen
snprintf
__ctype_b
__rawmemchr
__strtol_internal
getpid
fscanf
fgets
...
csh> netstat TCP Local Address Remote Address Swind Send-Q Rwind Recv-Q State -------------------- -------------------- ----- ------ ----- ------ ------- iesun7.telnet banpc17.1040 32120 0 10136 0 ESTABLISHED iesun7.40590 ieug0.50819 64240 0 8760 0 ESTABLISHED iesun7.560 ieug0.nfsd 64240 0 8760 0 ESTABLISHED iesun7.22 iest26.1022 8760 0 8760 20 ESTABLISHED iesun7.40709 eng.32771 8760 0 8760 0 TIME_WAIT iesun7.559 iest0.nfsd 8760 0 8760 0 ESTABLISHED iesun7.40710 eng.32771 8760 0 8760 0 TIME_WAIT iesun7.558 eng.nfsd 8760 0 8760 0 ESTABLISHED iesun7.557 ieugb.nfsd 8760 0 8760 0 ESTABLISHED Active UNIX domain sockets Address Type Vnode Conn Local Addr Remote Addr 30000d3f7f0 stream-ord 30000b2a948 00000000 ssh-14363-agent 30000d3fb20 stream-ord 00000000 00000000 30000d3fcb8 stream-ord 30000b2b488 00000000 /tmp/.X11-unix/X0
csh> traceroute www.ust.hk traceroute to www.ust.hk (143.89.14.34), 30 hops max, 38 byte packets 1 ntec-fw (192.168.64.254) 0.268 ms 0.170 ms 0.148 ms 2 router99.ie.cuhk.edu.hk (137.189.99.254) 0.833 ms 0.860 ms 0.767 ms 3 137.189.200.250 (137.189.200.250) 1.402 ms 1.270 ms 1.383 ms 4 globalone-FE.hkix.net (202.40.161.32) 3.292 ms 3.097 ms 3.052 ms 5 204.59.89.14 (204.59.89.14) 3.191 ms 2.911 ms 2.840 ms 6 192.245.196.214 (192.245.196.214) 5.038 ms 5.080 ms 4.657 ms 7 internet-gw1.ust.hk (202.40.138.117) 5.052 ms 5.463 ms 4.940 ms 8 www.ust.hk (143.89.14.34) 4.753 ms * 4.872 ms
csh> /sbin/arp ntec14 Address HWtype HWaddress Flags Mask Iface ntec14 ether 00:D0:09:28:9F:79 C eth0 csh> /sbin/arp -a ntec14 (192.168.64.14) at 00:D0:09:28:9F:79 [ether] on eth0 pntec11 (172.18.1.11) at 00:D0:09:44:C2:7C [ether] on eth0 ntec92 (192.168.128.92) at 00:D0:09:28:31:69 [ether] on eth0 ntec93 (192.168.128.93) at 00:D0:09:2A:49:08 [ether] on eth0 ntec15 (192.168.64.15) at 00:D0:09:4D:9F:D6 [ether] on eth0 ntec12 (192.168.64.12) at 00:D0:09:28:3B:1C [ether] on eth0 ntec94 (192.168.128.94) at 00:D0:09:2D:6F:03 [ether] on eth0 victim (192.168.128.50) at 00:D0:09:27:66:18 [ether] on eth0 ntec13 (192.168.64.13) at 00:D0:09:2D:D8:2A [ether] on eth0 ntec95 (192.168.128.95) at 00:D0:09:4E:46:0C [ether] on eth0 ntec88 (192.168.128.88) at 00:D0:09:4E:46:13 [ether] on eth0 ...
csh> /sbin/accton /var/log/pacct csh>lastcomm clear user3 stdout 0.00 secs Wed Oct 4 19:46 lastcomm user3 stdout 0.22 secs Wed Oct 4 19:46 stty user3 stdout 0.01 secs Wed Oct 4 19:46 bash F user3 stdout 0.00 secs Wed Oct 4 19:46 tput user3 stdout 0.00 secs Wed Oct 4 19:46 bash F user3 stdout 0.00 secs Wed Oct 4 19:46 tput user3 stdout 0.01 secs Wed Oct 4 19:46 grep user3 stdout 0.00 secs Wed Oct 4 19:46
csh> cat .bash_history more .bashrc exit ls tcsh ls lastcomm man lastcomm which acct exit ls ls -l ls -lFa more .tschrc ..
csh> find . -mtime -1 -type f -print | xargs ls -l -rw------- 1 shlam daemon 68215 Jun 9 10:10 ./ltrace_0.3.10.tar.gz -rw------- 1 shlam daemon 44933 Jun 9 16:10 ./www.hack.com.tar.gz (find the file that modified lesser than a day) csh> ls -lut lrwxrwxrwx 1 shlam daemon 2 Jun 9 17:52 m5 -> mm drwxrwxr-x 2 shlam root 104 Jun 9 17:50 .X11-pipe/ drwxrwxr-x 2 shlam root 104 Jun 9 17:50 .X11-unix/ drwxrwxrwx 2 root root 107 Jun 9 17:50 .pcmcia/ drwxrwxrwt 2 root root 161 Jun 9 17:50 .rpc_door/ drwx--x--x 7 shlam daemon 1052 Jun 9 17:50 autofs-3.1.5/ drwx--x--x 2 shlam daemon 683 Jun 9 17:50 forensic/ (list the more recent asscess file and directory)Note. Do not draw conclusion form MAC time stamp hastily becasue MAC time stamp can be forged easily.
# Log anything (except mail) of level info or higher. # Don't log private authentication messages! *.info;mail.none;news.none;authpriv.none /var/log/messages # The authpriv file has restricted access. authpriv.* /var/log/secure # Log all the mail messages in one place. mail.* /var/log/maillog # Everybody gets emergency messages, plus log them on another # machine. *.emerg * # Save mail and news errors of level err and higher in a # special file. uucp,news.crit /var/log/spooler # Save boot messages also to boot.log local7.* /var/log/boot.logNote. Log files can easily be erased or forged. Hence, besides looking for anything unusual entries in the log files, we should also look for any abnormal log entry absence.
Check the consistency among your log files too. For example, if your NDIS log file show that there were lots of www traffic to your host, but your host httpd access.log does not show that. Then some of your httpd access.log entries may be erased.
csh> nm -p /usr/local/sbin/sshd|more
0804a424 t gcc2_compiled.
0804a430 t gcc2_compiled.
08076d84 d p.2
08078a90 ? __DTOR_LIST__
08076d88 d completed.3
0804a430 t __do_global_dtors_aux
08078a84 ? __EH_FRAME_BEGIN__
0804a478 t fini_dummy
08078dc0 b object.8
0804a480 t frame_dummy
0804a4a0 t init_dummy
.....
csh> nm -Du /usr/local/sbin/sshd | more
__assert_fail
__deregister_frame_info
__errno_location
__gmon_start__
__libc_start_main
__lxstat
__register_frame_info
__strtol_internal
__xstat
abort
accept
alarm
bind
calloc
cfgetispeed
cfgetospeed
cfsetispeed
cfsetospeed
chdir
chmod
chown
clock
....


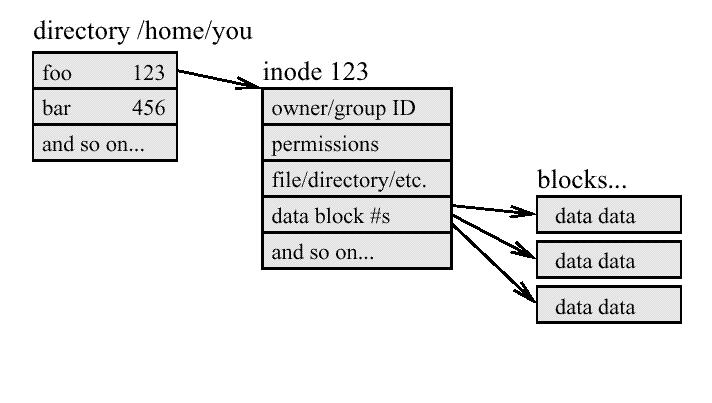
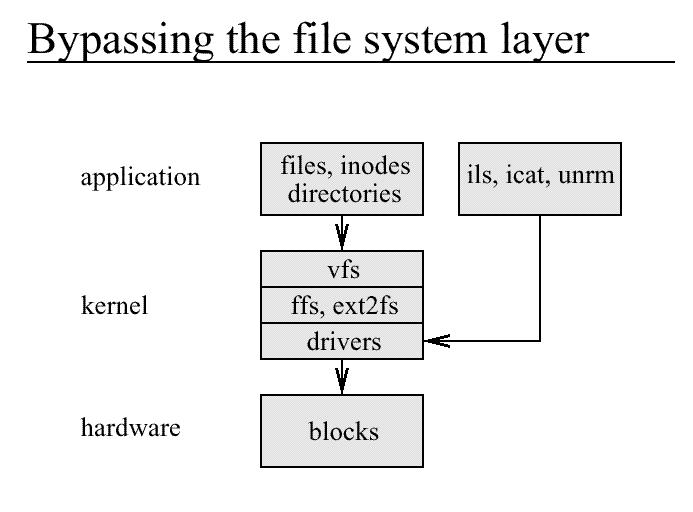
od -cx directory
ils inode
icat /dev_name inode > outfile
ntec5:/tmp/tt> ls
./ ../ abcdefg hijklmn
ntec5:/tmp/tt> cat abcdefg
Hello.
This is a testing.
Bla... Bla... testing
testing
ntec5:/tmp/tt> rm abcdefg
rm: remove `abcdefg'? y
ntec5:/tmp/tt> ls
./ ../ hijklmn
(see the current directory inode)
ntec5:/tmp/tt> ls -i
198049 ./ 160321 ../ 198054 hijklmn
(see the file system device)
ntec5:/tmp/tt> df
Filesystem 1k-blocks Used Available Use% Mounted on
/dev/hda3 2016044 1463012 450620 76% /
(view the removed file inode)
ntec5:/tmp/tt> icat /dev/hda3 198049|od -cx
0000000 ¡ 005 003 \0 \f \0 001 002 . \0 \0 \0 A r 002 \0
05a1 0003 000c 0201 002e 0000 7241 0002
0000020 0 \0 002 002 . . \0 \0 ¢ 005 003 \0 024 \0 \f 001
0030 0202 2e2e 0000 05a2 0003 0014 010c
0000040 . h i j k l m n . s w p £ 005 003 \0
682e 6a69 6c6b 6e6d 732e 7077 05a3 0003
^^^^^^^^^
(198051)
0000060 020 \0 \a 001 a b c d e f g p ¦ 005 003 \0
0010 0107 6261 6463 6665 7067 05a6 0003
0000100 Ä 017 \a 001 h i j k l m n n . s w p
0fc4 0107 6968 6b6a 6d6c 6e6e 732e 7077
(retrive the removed by icat)
ntec5:/tmp/tt> icat /dev/hda3 198051
Hello.
This is a testing.
Bla... Bla... testing
testing
(list the removed inode)
ntec5:/tmp/tt> ils /dev/hda3 198051
class|host|start_time
ils|ntec5|960574486
inum|allocation|uid|gid|m_time|a_time|c_time|dtime|mode|links|size|block0|block1
198051|f|0|0|960574079|960574139|960574162|960574162|100644|0|60|418630|0
^^ (links = 0)
ntec5:/tmp/tt> ls -i
198049 ./ 160321 ../ 198054 hijklmn
ntec5:/tmp/tt> ils /dev/hda3 198054
class|host|start_time
ils|ntec5|960574631
inum|allocation|uid|gid|m_time|a_time|c_time|dtime|mode|links|size|block0|block1
198054|a|0|0|960574099|960574099|960574099|0|100644|1|25|418631|0
Linux Root Kit V contains the follow program bindshell port/shell type daemon! chfn Trojaned! User->r00t chsh Trojaned! User->r00t crontab Trojaned! Hidden Crontab Entries du Trojaned! Hide files find Trojaned! Hide files fix File fixer! ifconfig Trojaned! Hide sniffing inetd Trojaned! Remote access killall Trojaned! Wont kill hidden processes linsniffer Packet sniffer! login Trojaned! Remote access ls Trojaned! Hide files netstat Trojaned! Hide connections passwd Trojaned! User->r00t pidof Trojaned! Hide processes ps Trojaned! Hide processes rshd Trojaned! Remote access sniffchk Program to check if sniffer is up and running syslogd Trojaned! Hide logs tcpd Trojaned! Hide connections, avoid denies top Trojaned! Hide processes wted wtmp/utmp editor! z2 Zap2 utmp/wtmp/lastlog eraser! sshd backdoored sshd-2.0.13 su backdoored su