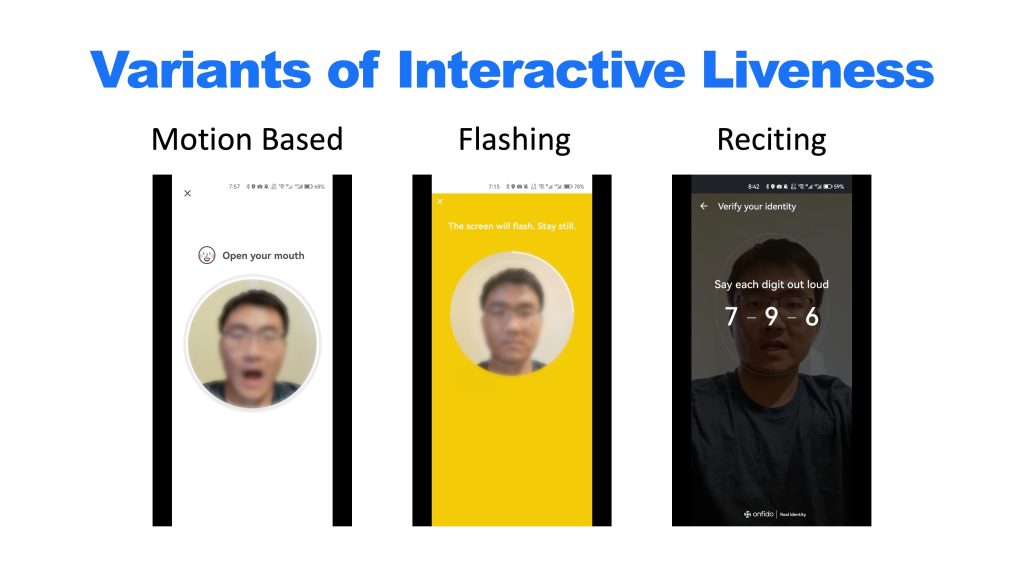
The use of facial recognition technology has become prolific, and with the rise of Wi-Fi and virtual private networks (VPNs), their security has become a hot-button topic. Two research teams from The Department of Information Engineering have recently revealed security vulnerabilities in mobile facial recognition software and enterprises’ Wi-Fi and VPN setups that have a real-world impact.
A team led by Prof. LAU Wing-cheong analysed 18 mobile facial recognition software development kits (SDKs), including those from industry leaders, and revealed security flaws in 11 of them that can result in liveness detection bypasses. After building an automatic app analyser to scan more than 18,000 apps, it was found that around 300 contained at least one of the vulnerable facial recognition libraries. By exploiting design flaws in the SDKs, an attacker can circumvent facial identification using only static photos of the victim. The team recently presented its findings at the Black Hat USA 2023 conference, under the title “The Living Dead: Hacking Mobile Face Recognition SDKs with Non-Deepfake Attacks”.
Another team led by Prof. CHAU Sze-yiu conducted in-depth testing and analysis of enterprise Wi-Fi and VPNs. The team discovered several design and implementation flaws in mainstream operating systems, which force users to adopt insecure wireless network settings, making them susceptible to attacks. More than 7,000 Wi-Fi setup guides from more than 2,000 colleges and universities around the world had been analyzed and it was found that about 86% instruct users to adopt unsafe Wi-Fi settings on at least one mainstream operating system. With VPNs, the team tested 132 front-end applications used around the globe and found serious yet previously unknown vulnerabilities in 63. These vulnerabilities allow hackers to steal user passwords easily and stealthily. In addition, the front-end applications of some VPN products allow a network attacker to execute arbitrary malicious code with high privileges on the user’s device, compromising the entire system. The research team also analysed about 2,000 VPN user manuals from universities worldwide and found configuration issues in more than 300 of them, which could make users fall into traps and have their passwords stolen by hackers.
Given the severity of these findings, the research team has made various safety recommendations to people affected and informed a number of local and foreign institutions about the defects. This research has led to the publication of three papers at well-known international academic conferences. The team was given the Best Paper Award at the 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks (ACM WiSec 2023).
More details can be found on the following conference briefing and papers:
- The Living Dead: Hacking Mobile Face Recognition SDKs with Non- Deepfake Attacks
- Back to School: On the (In)Security of Academic VPNs
- The Devil is in the Details: Hidden Problems of Client-Side Enterprise Wi-Fi Configurators
- All your Credentials are Belong to Us: On Insecure WPA2-Enterprise Configurations